One EASM platform for complete coverage
See your organization's current security state, understand what you're exposing, quickly resolve vulnerabilities and issues, and validate that your organization is following security policies, all in one External Attack Surface Management (EASM) platform for complete attack surface coverage.
Why choose EASM over Application Security tooling
Implementing an EASM tool doesn't require a new security budget. Instead, EASM is an excellent alternative to current Application Security tooling, particularly in addressing the need for AppSec teams to work with developers for quicker remediation.
See the current state of security in your organization
Get an overall state of security in your organization and drill down into specific aspects of your attack surface, such as your most critical web applications and security policies.
Impact of using EASM
- Get an overall current state of your attack surface
- Know that your most business-critical apps are secured
- Continuously discover unknown assets through automation
- Test each asset for vulnerabilities and issues

Understand what you're exposing on your attack surface
See what your organization exposes to the Internet and how assets are protected, such as which assets are scanned and the types of vulnerabilities on those assets.
Impact of using EASM
- Know what is in your scope, what's being scanned, and the status of the scans
- Understand what types of vulnerabilities may be present on your assets

Quickly resolve vulnerabilities and issues
Understand what needs fixing, give developers the correct information to resolve critical issues, and don't delay them from shipping code.
Impact of using EASM
- No more slowing down developers - resolve issues quickly
- Managing security tooling requires minimal time and can be done via an API or integration
- Know where to take action first

Validate that your organization is following security policies
Not everything on your attack surface is a vulnerability. Spot anomalies across your organization's attack surface that your team can follow up on.
Impact of using EASM
- Make sure your team follows your unique set of internal security policies
- Discover security headers and unapproved tech through automation

How does Detectify work? Watch a short demo
With strong foundations in Application Security and Vulnerability Management, we use DAST methodology in our Surface Monitoring and Application Scanning products, which together form our EASM platform. Watch this short product demo for an introduction to the platform.
Discover our platform's products
One platform for comprehensive coverage of your attack surface
Surface Monitoring
Continuously discover and monitor all Internet-facing assets that you host with Surface Monitoring.
Cover your entire public DNS footprint, including ports
No complex configurations to get started
Fingerprint your tech stack
Application Scanning
Find and remediate business-critical vulnerabilities in custom-built apps with advanced crawling and fuzzing.
Render and crawl a custom-built application for in-depth findings
Maintain state and test authenticated areas
Scan massive applications with smart page filters
Broader and deeper coverage
A platform that provides complete coverage across the external attack surface
Surface Monitoring gives a comprehensive view of your attack surface, while Application Scanning provides deeper insights into custom-built applications. We recommend combining both products for the most comprehensive attack surface coverage.
Detectify features
Discover some of the platform's features
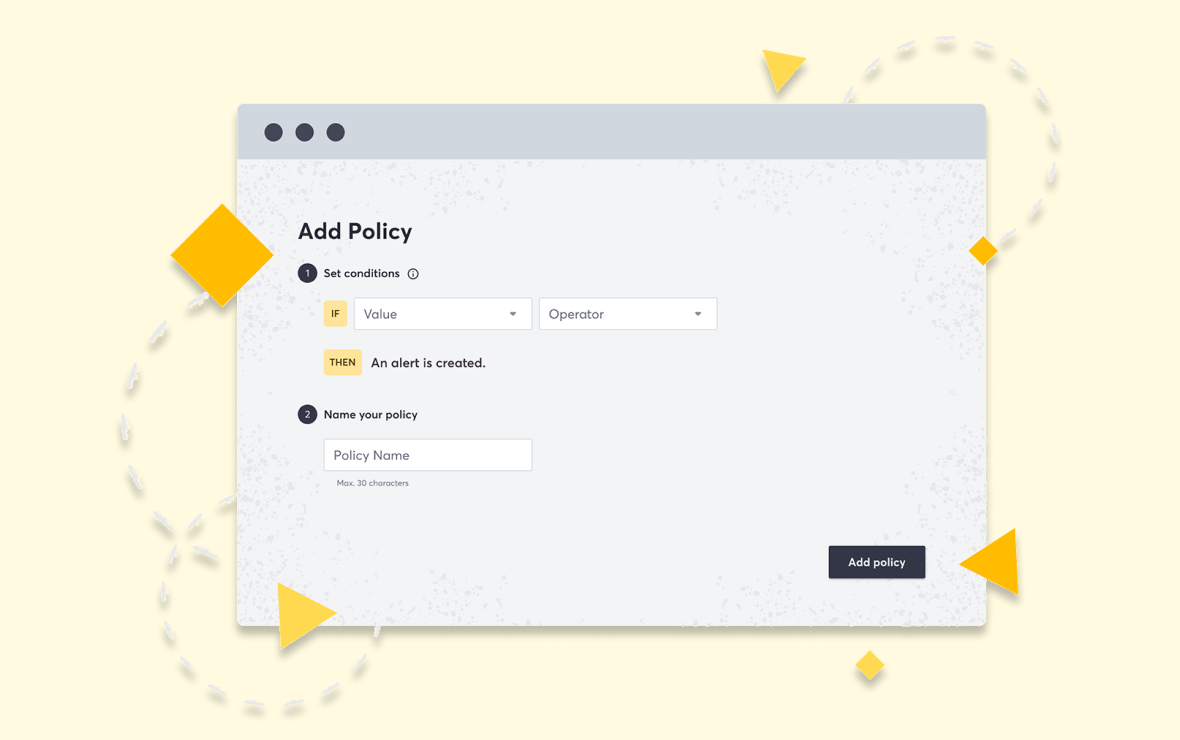
Attack Surface Custom Policies
Proactively reduce risk by setting, enforcing, and scaling customizable security policies across your attack surface.
- Validate that your security policies are implemented
- Ensure security headers are enforced
- Spot technologies that aren’t approved for us
- Catch unintended open ports across your attack surface
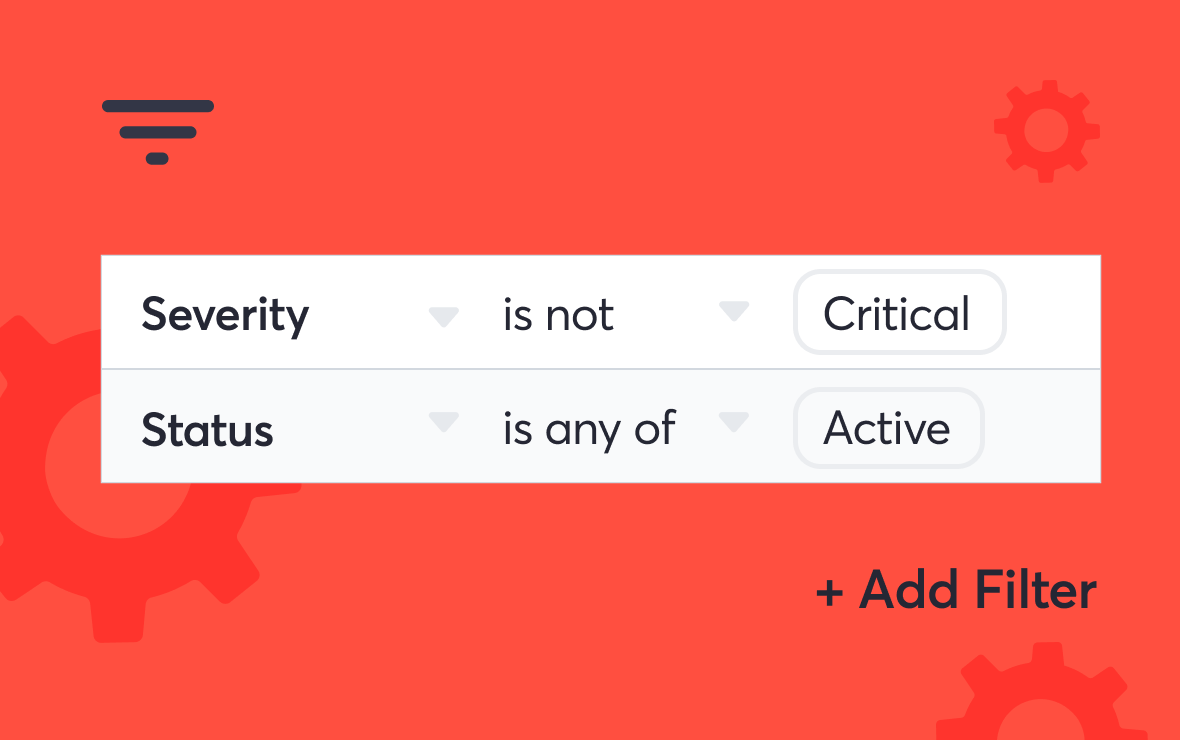
Vulnerabilities page
View, sort, filter, and export findings
Get an overview of the current state of the vulnerabilities on your attack surface.
- Combine multiple filters to narrow down vulnerability information
- Address threats on your web applications that matter the most
- Export findings when needed
- Suppress findings that aren’t an issue and mark them as an acceptable risk
- Filter for specific vulnerability types or severity scores
Vulnerabilities page
Groups for efficient bulk vulnerability management
- Organize assets in multiple ways, for instance, per technology, responsibility, or priority
- Take bulk action on up to 500 vulnerabilities at a time and easily change their status
Attack Surface View
Get a complete overview of your assets
- Access all your assets, technologies, and root assets on one page
- Five different levels of ‘Surface State’ indicate to what level an asset is exposed on your attack surface

Integrations / API
Customizable integrations and effective triaging of vulnerability findings
- Centralize vulnerability findings in one place, such as through a Vulnerability Management (VM) platform
- Pre-set integrations with popular tools, including Slack, Jira, Trello, Microsoft Teams, Splunk, OpsGenie, and HTTP webhooks
- Customize how you work with vulnerability data, reducing noise and remediating faster